If you haven’t already, go install this month’s Windows security update asap
In brief: If you haven’t done this already, stop what you’re doing and install the latest Patch Tuesday update. Then come back and read about how important this really is—no less than 87 security flaws ranging from important to critical have been fixed in several Microsoft products. That includes fixes for the infamous PrintNightmare and an Office zero-day vulnerability that’s being actively exploited in the wild.
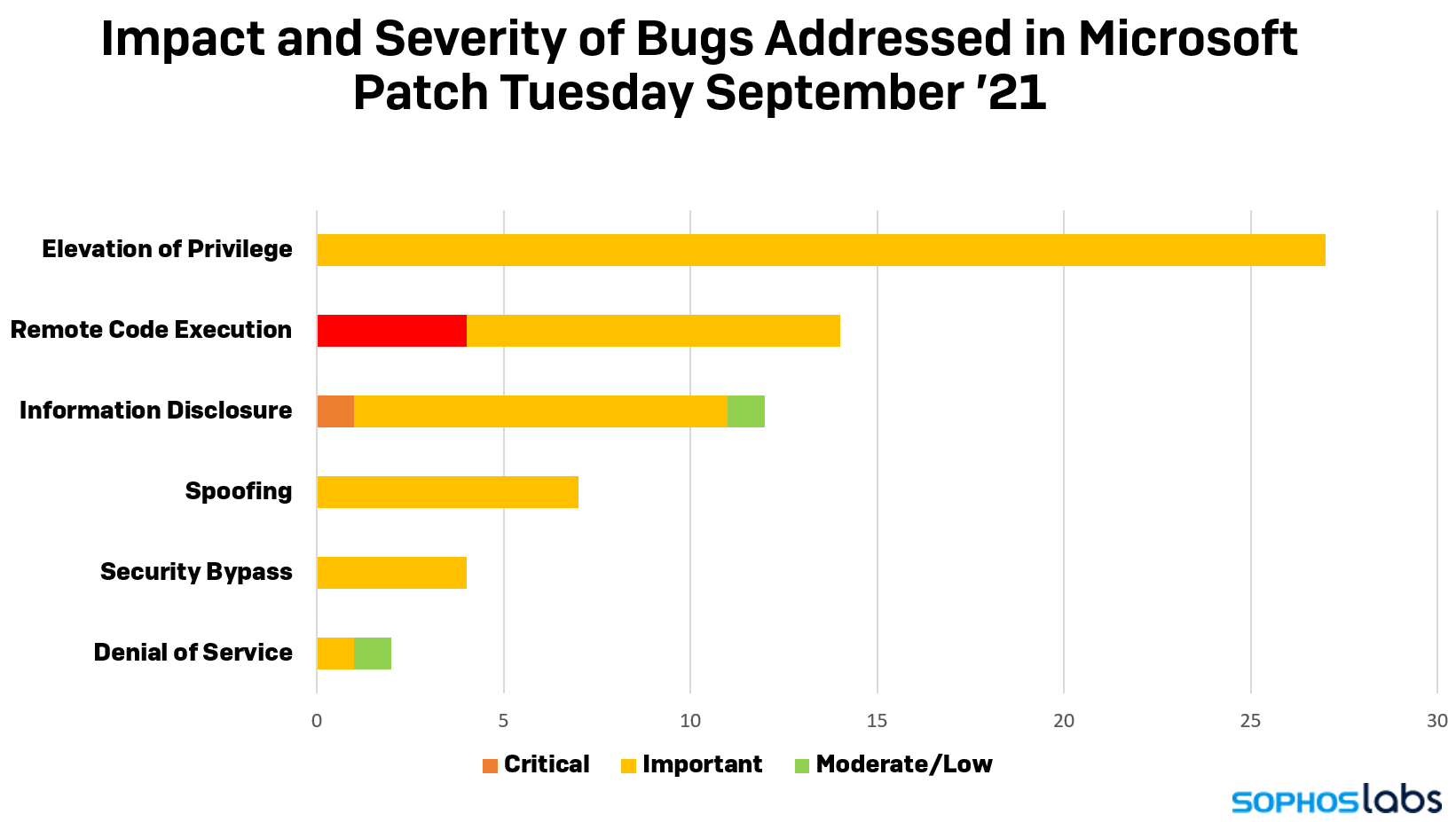
This month’s Patch Tuesday update may be light as a feather, but don’t let that fool you. Microsoft has included fixes for no less than 67 security vulnerabilities—87 if you count several fixes for holes in the Chromium-based Microsoft Edge. The flaws affect several Microsoft products, including Windows, Windows DNS, the Windows Subsystem for Linux, Visual Studio, Office, SharePoint Server, Edge, and Azure.
Most notably, the update fixes one zero-day Office flaw (CVE-2021-40444) that hackers are actively exploiting. News first broke about this a week ago, but Microsoft wasn’t able to release an out-of-band patch at the time. The issue is related to an attack method that uses malicious Office files that is extremely easy to perform and 100 percent reliable. Upon opening a file, Office will take users to a web page via Internet Explorer that automatically downloads malware on your computer.
The exploit is possible due to a bug in the MSHTML component of Microsoft Office used to render browser pages in the context of a Word file. Windows 7, Windows 10, and Windows Server versions 2008 and above are all affected.
Also included in the security update are fixes for a trio of CVEs that affect the Windows Common Log File System Driver—CVE-2021-36955, CVE-2021-36963, and CVE-2021-38633. These are privilege escalation vulnerabilities that could allow an attacker (say, a ransomware operator) to make changes to your PC and affect all versions of Windows. Fortunately, there’s been no indication that they’ve been exploited in the wild.

Furthermore, Microsoft has plugged four privilege escalation flaws recently uncovered in the Print Spooler service in Windows 10. These are filed under CVE-2021-38667, CVE-2021-36958, CVE-2021-38671, and CVE-2021-40447.
Companies using Windows 7, Windows Server 2008, and Windows Server 2008 R2 should also install this patch, as it includes a fix for CVE-2021-36968—an elevation of privilege vulnerability present in Windows DNS that is easy to exploit and doesn’t require user interaction.
Other companies have also released security updates that users should install as soon as possible. Apple has updates that fix a major zero-click vulnerability in all of its operating systems. Adobe has several security updates that affect its Creative Cloud products. Google has fixes for important and critical flaws in Android. Security teams should review the latest security updates from Cisco, SAP, Citrix, Siemens, Schneider Electric, Oracle Linux, SUSE, and Red Hat.
